1) The legal framework
The security measures that must be implemented by the controller to protect the processing of personal data carried out under their responsibility are set out in article 28 of the Law of 1 August 2018 on the protection of natural persons with regard to the processing of personal data in criminal and national security matters, as well as in article 32 of REGULATION (EU) 2016/679 OF THE EUROPEAN PARLIAMENT AND OF THE COUNCIL of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation).
2) Risk analysis
As prescribed by the legal framework, the Grand-Ducal Police has conducted a risk assessment and taken the necessary steps to minimise risks.
Risk analysis is a key aspect of information security and is conducted as part of managing the entity's information security management system. The risk analysis makes it possible to:
- identify information security risks;
- assess and appraise the risks identified;
- establish and limit adverse effects on information security;
- define and plan the actions to be implemented to tackle the risks;
- implement the actions planned;
- accept the residual risk;
- determine and apply an approach of continuous improvement to information security.
As the risk analysis contains details of the technical measures implemented, it cannot be published, as understanding the techniques used to protect the processing of personal data is obviously crucial information for a criminal looking to obtain illegal access to the processing.
The risk analysis conducted by the Police technologies department (Direction des technologies policières (PGD-DCRC-DTP)), version 1.0. final of 28 October 2018, hereinafter risk analysis v.1.0, is the entity's first formal information security risk analysis. It was conducted with a view to assessing the entity's current situation in terms of information security. Each risk has been carefully assessed against the information known and received from officers called upon from different departments, and the impact values of the C (confidentiality), I (integrity) and A (availability) criteria, the likelihood of a threat and the likelihood of a vulnerability.
2.1.) methodology:
The Grand-Ducal Police have adopted the risk analysis approach recommended by the National cybersecurity agency of France (ANSSI), where information forms a central part of the approach (data-centric model). To carry out its risk analysis, the entity uses the MONARC risk analysis tool, developed by CASES, hosted on the GovCloud platform implemented upstream by the Government IT centre (CTIE) subject to an agreement with ANSSI for hosting the Monarc tool, with ANSSI making it available for use. The benefit is that all the elements required to create the entity's model as a basis for the risk analysis are immediately available with the predetermined library objects (assets and risk scenarios) structured in line with the aforementioned approach. As a result, the analysis may be started quickly and conducted efficiently.
Risk analysis v.1.0 summarises the method and sets out the results of the risk assessment carried out using MONARC at the entity's work environment. MONARC is implemented in compliance with the international standard ISO/IEC 27005:2011.
References
[1] ISO/IEC 27005:2011 - Information security risk management.
[2]http://www.iso.org/iso/en/catalogue_detail?csnumber=56742. The ISO/IEC 27005 standard provides a detailed explanation of how to conduct the risk assessment and risk treatment, in relation to information security
2.2.) description of the "Méthode Optimisée d’Analyse des Risques CASES" (MONARC):
MONARC relies on a library of risk models providing objects made up from risk scenarios for assets or groups of assets. This approach helps to manage the most common risks and achieve objectivity and efficiency. As MONARC is entirely iterative, these results can be refined and tailored to the maturity of each entity by increasing the detail of the risk scenarios.
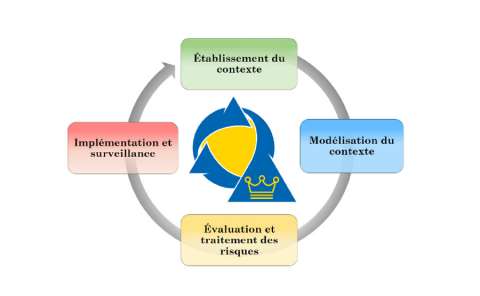
Context
The first step is to take stock of the context, challenges and priorities of the entity wishing to analyse its risks.
In particular, this serves to identify the entity's key activities and critical processes in order to steer the risk analysis towards the most important elements. To do this, a kick-off meeting is arranged with members of the management team and key individuals. The goal is to understand what makes the entity "live" and what could destroy it, as well as identifying the key processes, internal and external threats, and organisational, technical and human vulnerabilities.
Context modelling
This phase includes the modelling of object trees. Assets were identified in the previous phase. They must now be detailed and formalised in a diagram showing their interdependencies.
Impacts are defined at the level of the primary assets (information or services). The secondary assets inherit the impact of the primary asset to which they are attached (object tree).
The impacts at secondary asset level can be modified manually.
Assessment and treatment of risks
The assessment consists of quantifying the threats, vulnerabilities and impacts to calculate risks.
This requires quality information on the exact likelihood of the threats, the ease of exploiting vulnerabilities and potential impacts, etc.; hence the need to rely on metrics validated by experts.
When the risk assessment identifies a risk exceeding the acceptable level (risk acceptance grid), risk treatment measures should be implemented to reduce the risk to an acceptable level.
Implementation and monitoring
When the first treatment of risks has been carried out, an ongoing security management phase must be entered with monitoring and recurring control of security measures, in order to improve these sustainably.
This fourth phase also enables continuous optimisation of security by increasing the detail of objects used and expanding the scope of the risk analysis.
3) Consultant assessment
3.1.) strengths:
- The commitment by the management at the Central directorate for resources and competences (Direction centrale "ressources et compétences" - DCRC) to conducting a risk analysis for the Police technologies department (Direction des technologies policières - DTP), entrusting the handling of the analysis to DTP agents and acquiring internal knowledge and skills in information security.
- Assigning a study brief and logical access management to a DTP agent.
- Appointing a DPO at the entity.
3.2.) weaknesses:
- The time taken to carry out the risk analysis. The risk analysis should be considered a snapshot of the entity's situation at a given moment, so a long interval between the start and end of the analysis may compromise the results if changes have occurred in the meantime. Of course, the time it takes to run the risk analysis is also contingent on the availability of the people carrying it out.
3.3.) summary:
The consultants found the partners to be proactive and appreciate the management's determination to strive towards improving information security within their control.

